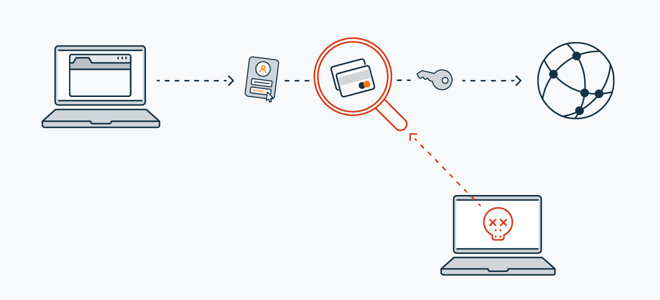
Fun Tips About How To Detect Network Sniffers
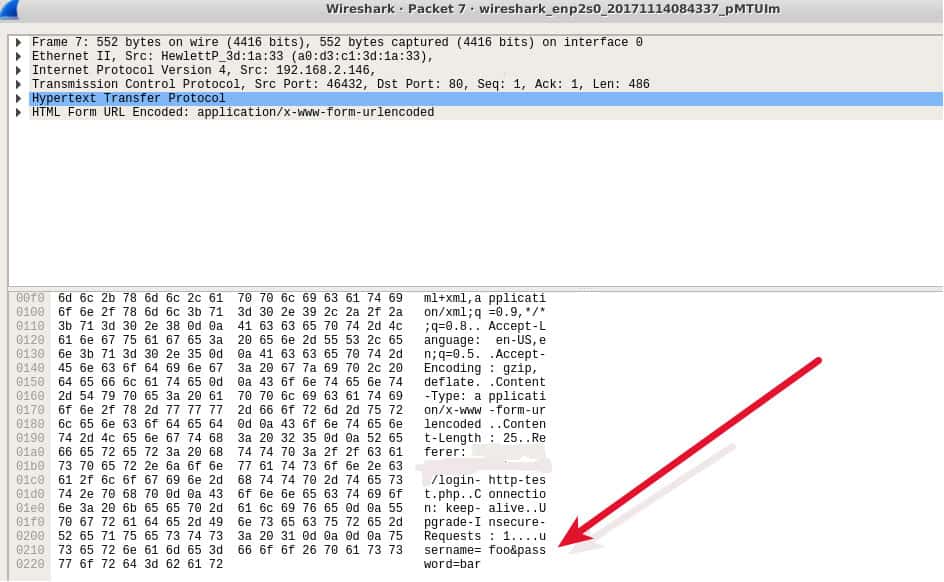
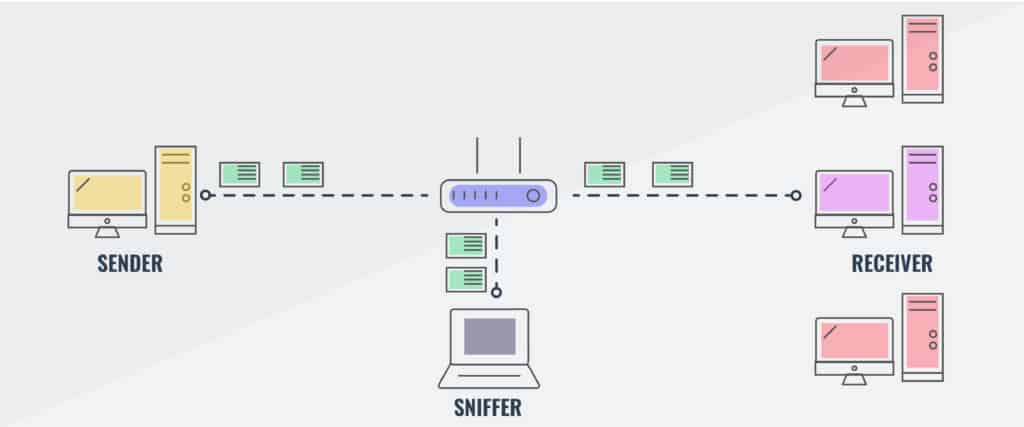
By using network sniffers to “sniff” the packets en route, a user can analyze the traffic via “passive sniffing” (i.e., snooping in on the inflight data) or “active sniffing” (i.e., directly.
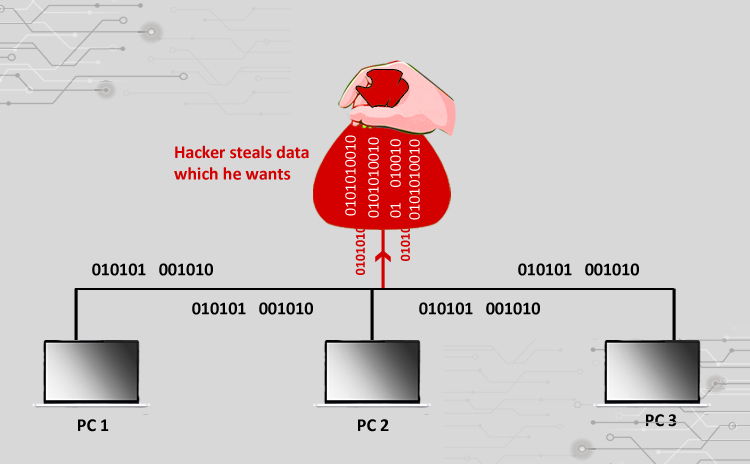
How to detect network sniffers. When installed on a computer a sniffer does generate some small amount of traffic — which allows. In the same network, we can use the network sniffing of zanti app to simulate the mimt attack of the selected target ip. Monitor mode means the wifi sniffer can intercept and read only incoming data without.
A sniffer can run in one of two modes: Any interface running in promiscuous mode is listening to all network traffic, a key indicator that a network sniffer is being used. The sniffer software needs to put a network device into promiscuous mode, which many operating systems can report.
If the system runs the sniffer, its interface will be in promiscuous mode. Any interface running in promiscuous mode is “listening” to all network traffic, a key indicator that a network sniffer is being used. A sniffer might not be connected to the network, and it might not be emitting any signal at all if it's just listening.
Passive smelling, as previously said, is extremely difficult to detect. Presence of strange traffic and at a high rate:. To check your interfaces using ifconfig, just.
The test works like this: How do you detect packet sniffer? There are two ways of using a wifi sniffer, in monitor and promiscuous mode.
Active sniffing is a little more evident, but you'll still need some. How to detect a sniffer on your network? Send a ping with the correct ip address into the network but with a wrong mac.
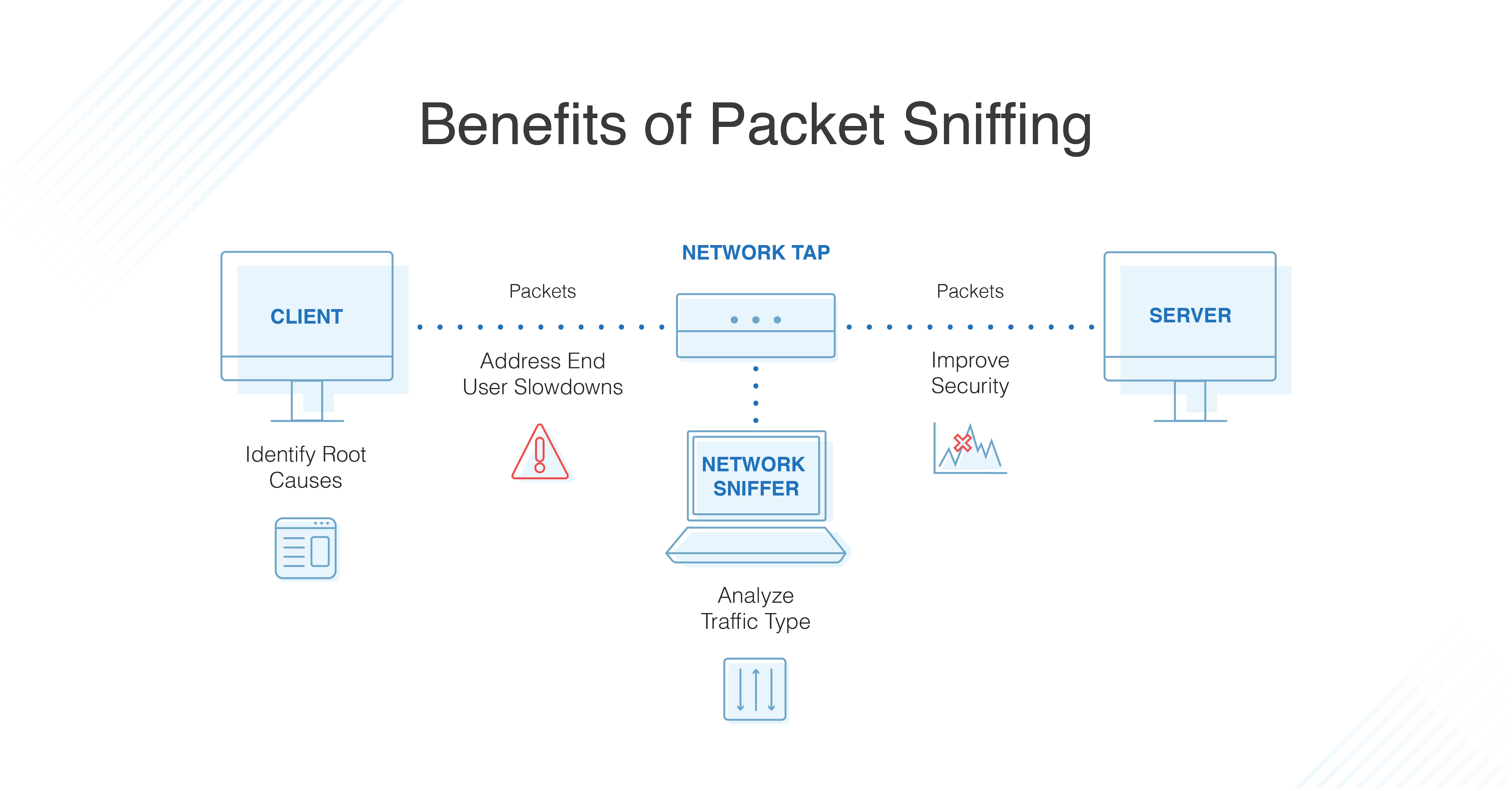













/what-is-a-packet-sniffer-2487312-a2b309516aa1492b88390593280f283b.png)